The SSL or TLS handshake enables the SSL or TLS client and server to establish the secret keys with which they communicate.
The steps that enable the SSL or TLS client and server to communicate with each other can be summarized as follows:
- Agree on the version of the protocol to use.
- Select cryptographic algorithms.
- Authenticate each other by exchanging and validating digital certificates.
- Use asymmetric encryption techniques to generate a shared secret key, which avoids the key distribution problem. SSL or TLS then uses the shared key for the symmetric encryption of messages, which is faster than asymmetric encryption.
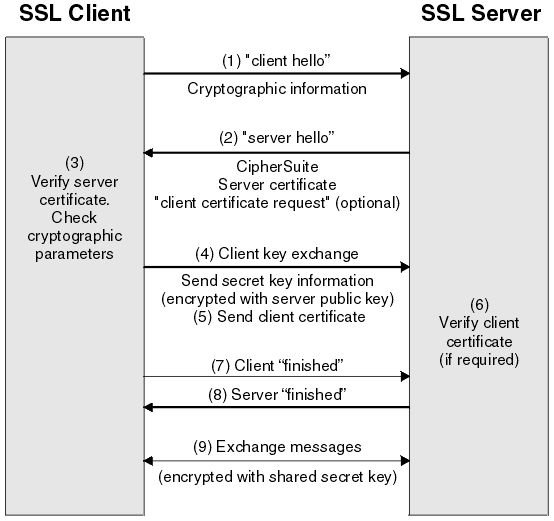
Full details of the messages that are exchanged during the SSL handshake are not provided, but in overview, the steps that are involved in the SSL handshake are as follows:
- The SSL or TLS client sends a "client hello" message that lists cryptographic information such as the SSL or TLS version and, in the client’s order of preference, the CipherSuites supported by the client. The message also contains a random byte string that is used in subsequent computations. The protocol allows for the "client hello" to include the data compression methods that are supported by the client.
- The SSL or TLS server responds with a "server hello" message that contains the CipherSuite chosen by the server from the list that is provided by the client, the session ID, and another random byte string. The server also sends its digital certificate. If the server requires a digital certificate for client authentication, the server sends a "client certificate request" that includes a list of the types of certificates that are supported and the Distinguished Names of acceptable Certification Authorities (CAs).
- The SSL or TLS client verifies the server’s digital certificate. For more information, see How SSL and TLS provide identification, authentication, confidentiality, and integrity.
- The SSL or TLS client sends the random byte string that enables both the client and the server to compute the secret key to be used for encrypting subsequent message data. The random byte string itself is encrypted with the server’s public key.
- If the SSL or TLS server sent a "client certificate request", the client sends a random byte string encrypted with the client’s private key, together with the client’s digital certificate, or a "no digital certificate alert". This alert is only a warning, but with some implementations the handshake fails if client authentication is mandatory.
- The SSL or TLS server verifies the client’s certificate. For more information, see How SSL and TLS provide identification, authentication, confidentiality, and integrity.
- The SSL or TLS client sends the server a "finished" message, which is encrypted with the secret key, indicating that the client part of the handshake is complete.
- The SSL or TLS server sends the client a "finished" message, which is encrypted with the secret key, indicating that the server part of the handshake is complete.
- For the duration of the SSL or TLS session, the server and client can now exchange messages that are symmetrically encrypted with the shared secret key.
Figure 1 illustrates the SSL or TLS handshake.
Figure 1. Overview of the SSL or TLS handshake