Cryptography is the process of converting between readable text, called plaintext, and an unreadable form, called ciphertext.
- The sender converts the plaintext message to ciphertext. This part of the process is called encryption (sometimes encipherment).
- The ciphertext is transmitted to the receiver.
- The receiver converts the ciphertext message back to its plaintext form. This part of the process is called decryption (sometimes decipherment).
The conversion involves a sequence of mathematical operations that change the appearance of the message during transmission but do not affect the content. Cryptographic techniques can ensure confidentiality and protect messages against unauthorized viewing (eavesdropping), because an encrypted message is not understandable. Digital signatures, which provide an assurance of message integrity, use encryption techniques. For more information, see Digital signatures in SSL and TLS.
- Algorithms that require both parties to use the same secret key. Algorithms that use a shared key are known as symmetric algorithms. Figure 1 illustrates symmetric key cryptography.
- Algorithms that use one key for encryption and a different key for decryption. One of these keys must be kept secret but the other can be public. Algorithms that use public and private key pairs are known as asymmetric algorithms. Figure 2 illustrates asymmetric key cryptography, which is also known as public key cryptography.
The encryption and decryption algorithms that are used can be public but the shared secret key and the private key must be kept secret.
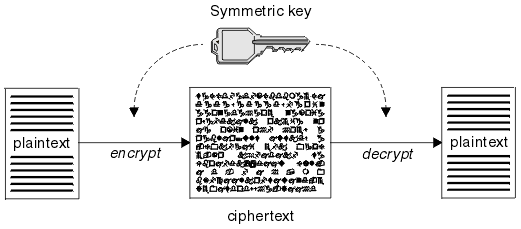
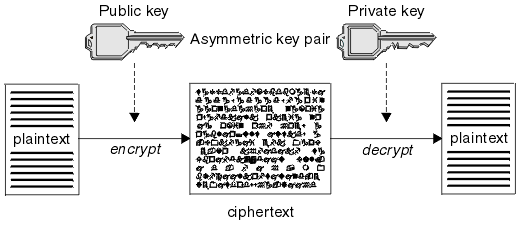
Figure 2 shows plaintext encrypted with the receiver’s public key and decrypted with the receiver’s private key. Only the intended receiver holds the private key for decrypting the ciphertext. The sender can also encrypt messages with a private key. Anyone who holds the sender’s public key can decrypt such messages, with the assurance that the messages must be from the sender.
With asymmetric algorithms, messages are encrypted with either the public or the private key, but can be decrypted only with the other key. Only the private key is secret. The public key can be known by anyone. With symmetric algorithms, the shared key must be known only to the two parties. This condition is called the key distribution problem. Asymmetric algorithms are slower but have the advantage that there is no key distribution problem.
Other terminology that is associated with cryptography is as follows:
- Block cipher algorithm
- These algorithms encrypt data by blocks. For example, the RC2 algorithm from RSA Data Security Inc. uses blocks 8 bytes long.
- Stream cipher algorithm
- These algorithms operate on each byte of data.